With a typical Sitecore site, updating the Site Definition configuration with the requiredLogin and loginPage attributes it's somewhat simple to get a site pointed to your Federated login page.
In SXA, it's not so straight forward unfortunately.
There are ultimately two main steps to getting your SXA site to point to the Sitecore Identity Server Azure AD page you setup previously.
Step 1 - Update Site Grouping
In Content Editor, navigate to your SXA site, then open up Settings and drill down until you find Site Grouping.
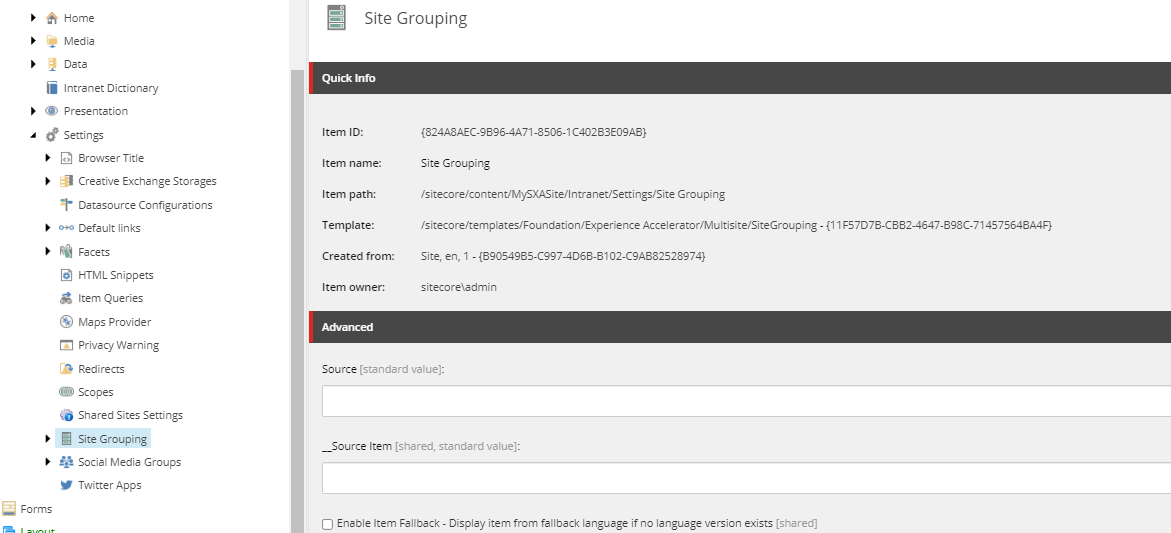
Open that up and you'll find an item with the same name as your SXA site. Click on the item and then scroll down to the Other Properties fields.
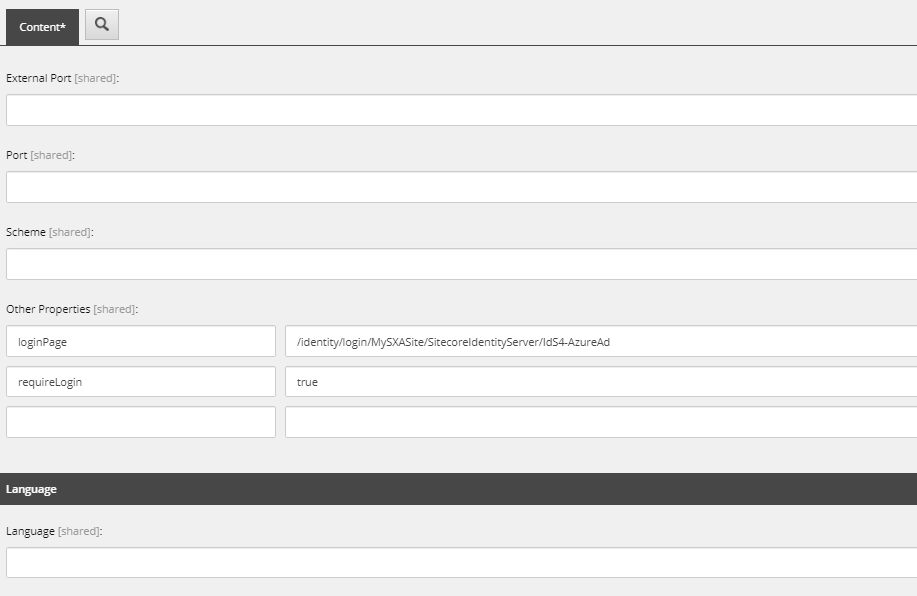
Update loginPage Attribute
In one of those files you'll enter in the login page. If you're connecting to the Azure AD instance you setup previously it will look familiar to how you entered it in the Site Definition configuration, except you'll need to have the full path.
The path in our example is: /identity/login/MySXASite/SitecoreIdentityServer/IdS4-AzureAd. Replace MySXASite with the name of your SXA site.
Update requiredLogin Attribute
In the next field, on one side put requiredLogin and on the otherside, true.
The reason we update it here and not below in the Login section is there you can only point to a Sitecore item as your login page and we need something more.
Save And Publish
With that updated, save it, publish it. That's step 1.
Step 2 - Updating The Map Entry Configuration
You may remember previously where we updated the <mapEntry> site list. When it comes to SXA sites, we need to do this again and explicitly call out the name of your SXA Site. Because the SXA sites are defined and organized differently, it's something that needs to be done.
My suggestion is to create a patch file similar to that which is below. Much of it should be familiar to you and might be something you have already from setting up Federated Authentication.
<configuration xmlns:patch="http://www.sitecore.net/xmlconfig/" xmlns:role="http://www.sitecore.net/xmlconfig/role/" xmlns:security="http://www.sitecore.net/xmlconfig/security/">
<sitecore role:require="Standalone or ContentDelivery or ContentManagement">
<federatedAuthentication type="Sitecore.Owin.Authentication.Configuration.FederatedAuthenticationConfiguration, Sitecore.Owin.Authentication">
<identityProvidersPerSites hint="list:AddIdentityProvidersPerSites">
<mapEntry name="MySXASite Site" type="Sitecore.Owin.Authentication.Collections.IdentityProvidersPerSitesMapEntry, Sitecore.Owin.Authentication">
<sites hint="list">
<site>MySXASite</site>
</sites>
<identityProviders hint="list:AddIdentityProvider">
<identityProvider ref="federatedAuthentication/identityProviders/identityProvider[@id='SitecoreIdentityServer']" id="SitecoreIdentityServer" />
</identityProviders>
<externalUserBuilder type="Sitecore.Owin.Authentication.Services.DefaultExternalUserBuilder, Sitecore.Owin.Authentication">
<IsPersistentUser>true</IsPersistentUser>
</externalUserBuilder>
</mapEntry>
</identityProvidersPerSites>
</federatedAuthentication>
</sitecore>
</configuration>
With that in place, restart your Sitecore instance and test it out.
